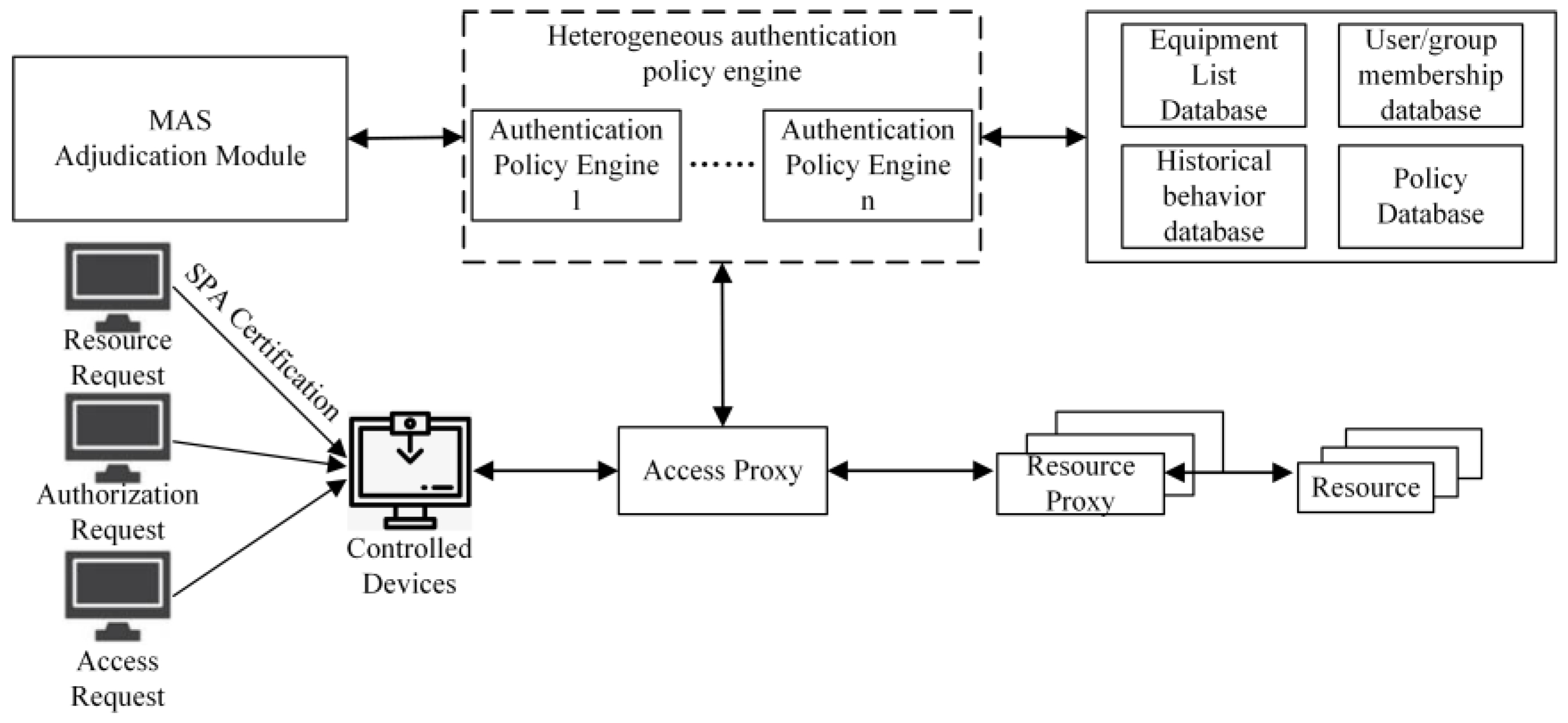
Electronics | Free Full-Text | Zero-Trust Security Authentication Based on SPA and Endogenous Security Architecture

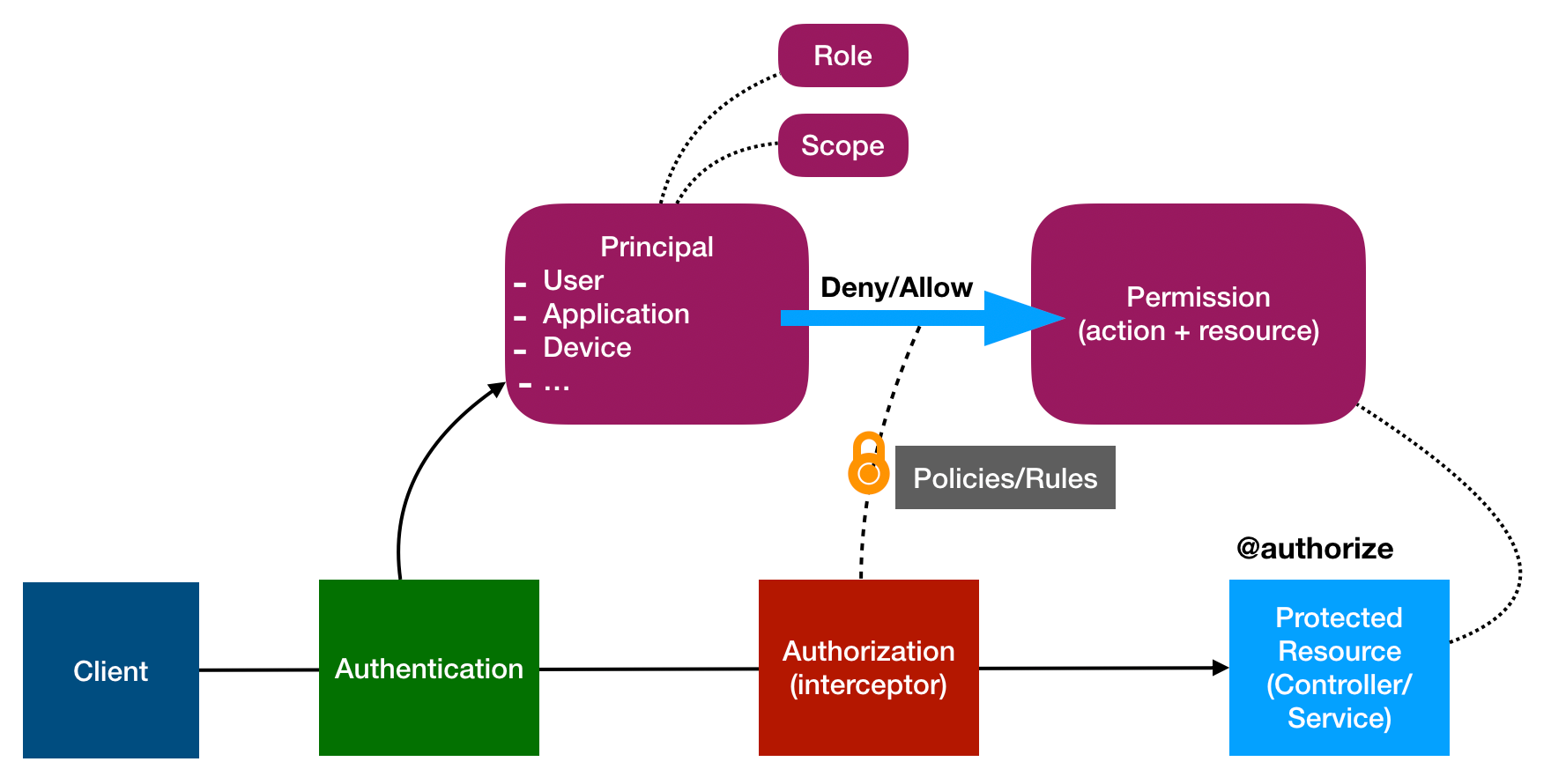
Amazon.fr - SAP Authorization System: Design and Implementation of Authorization concepts for SAP R/3 and SAP Enterprise Portals - IBM Business Consulting - Livres

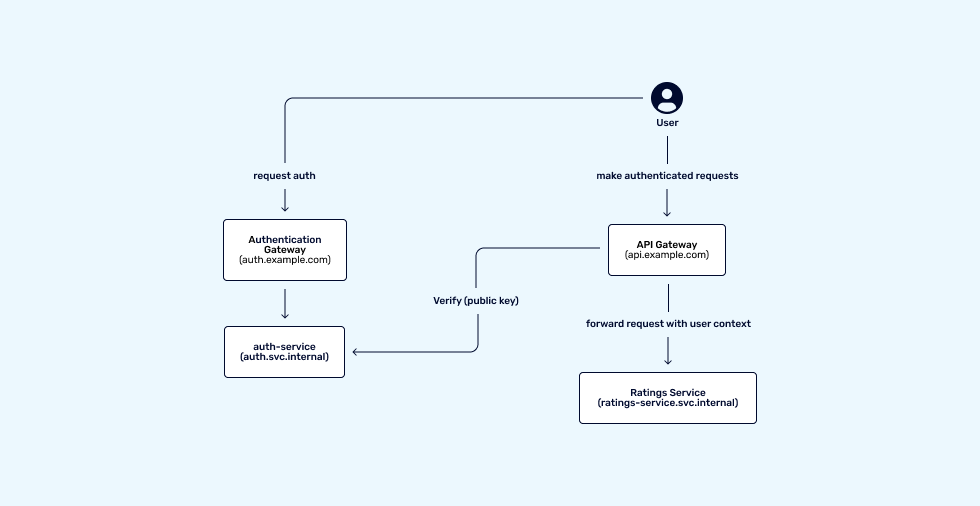

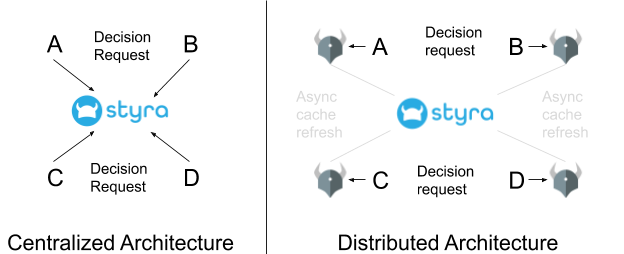


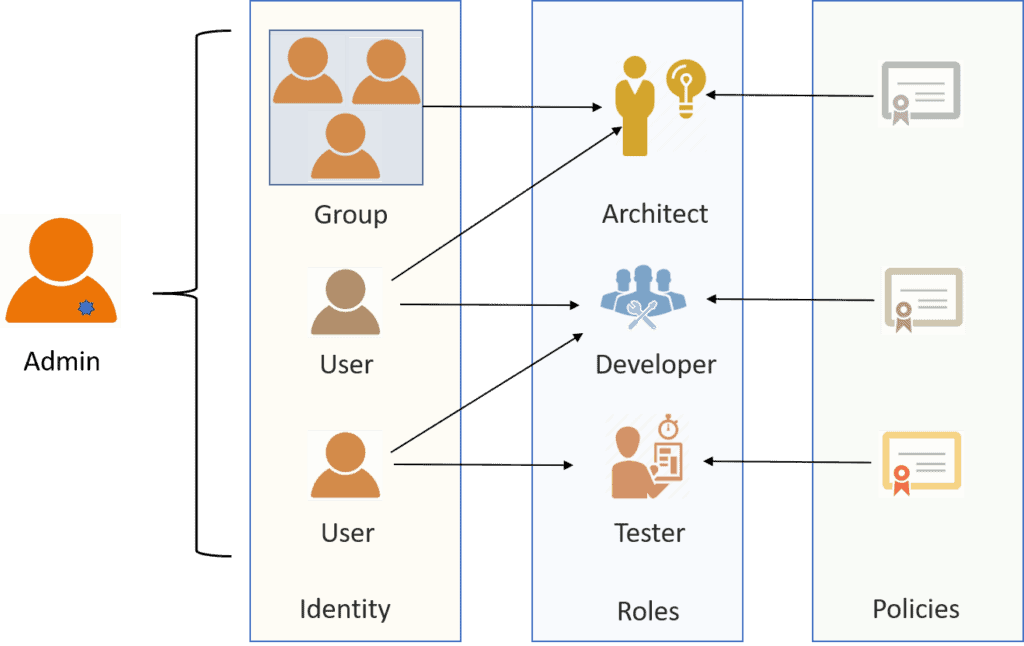
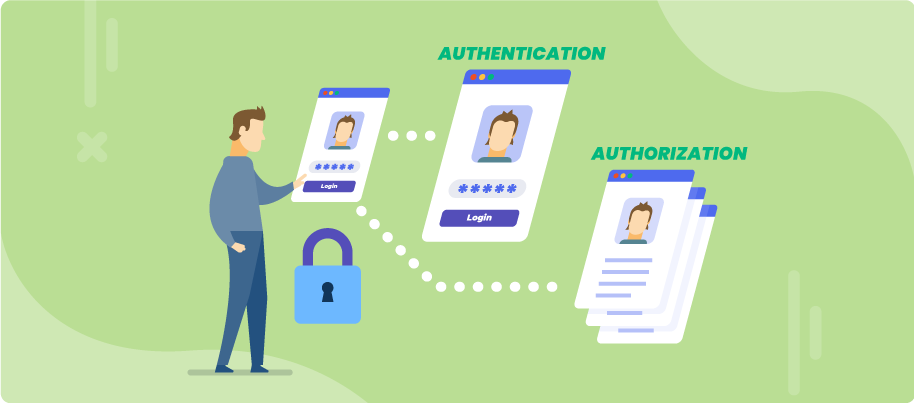
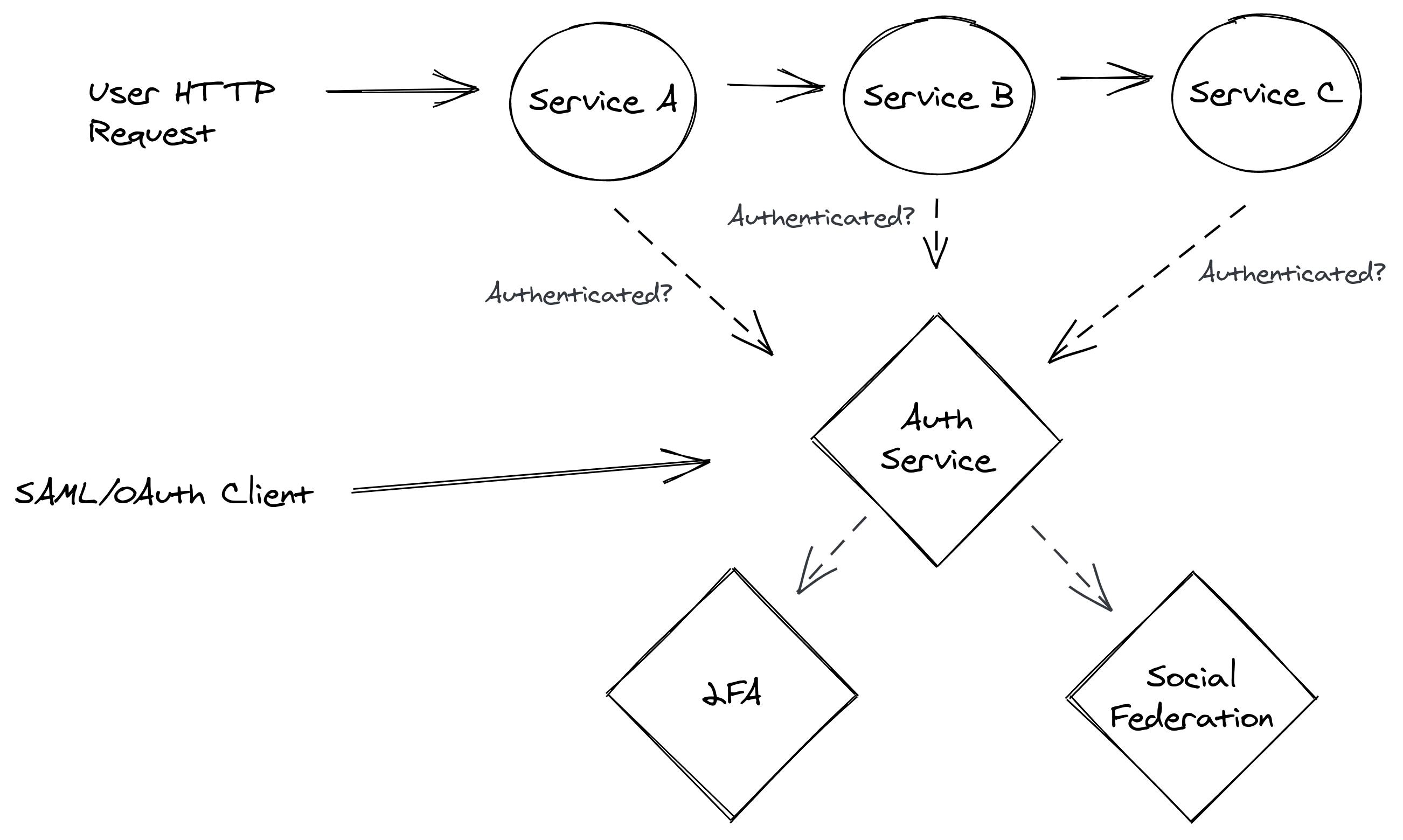

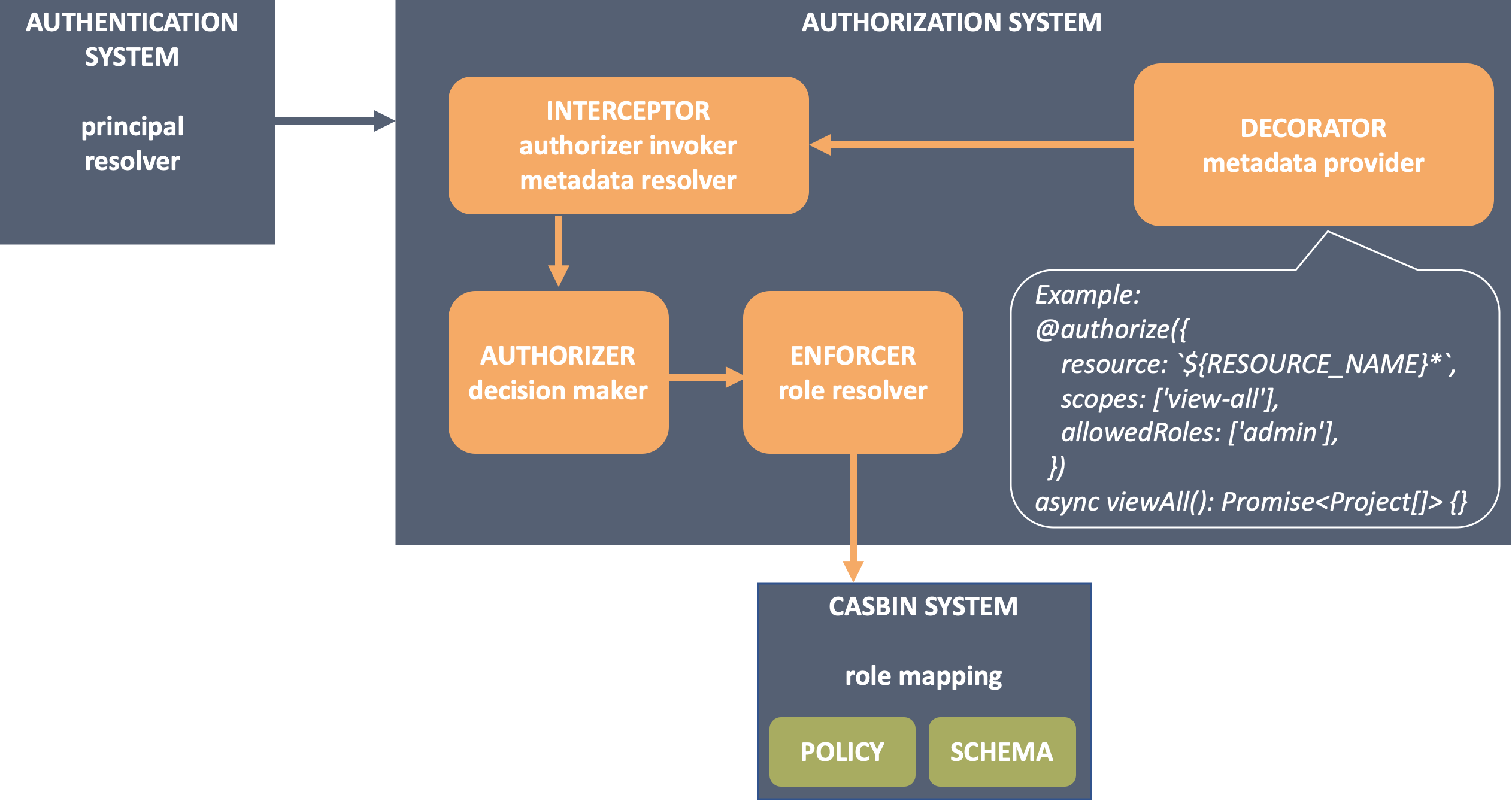

![ProjectManagement.com - 3 Levels of Project Work Authorization [Infographic] ProjectManagement.com - 3 Levels of Project Work Authorization [Infographic]](https://static.projectmanagement.com/images/blogs/project%20work%20authorization.png)
