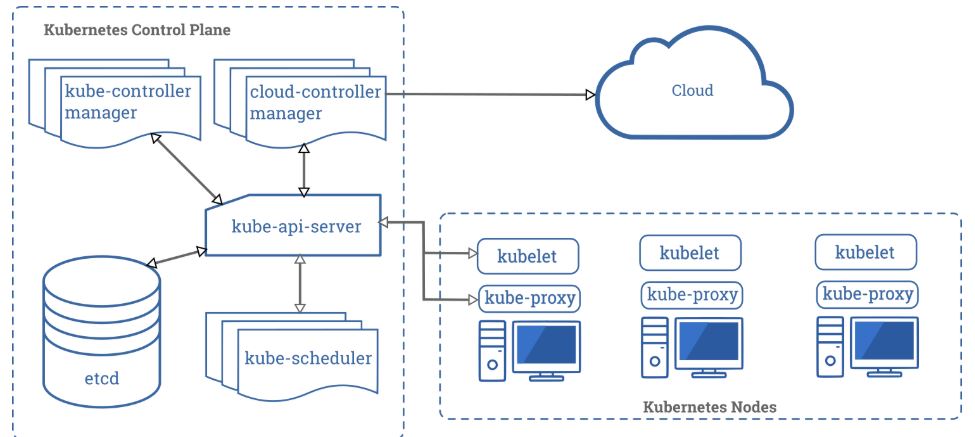
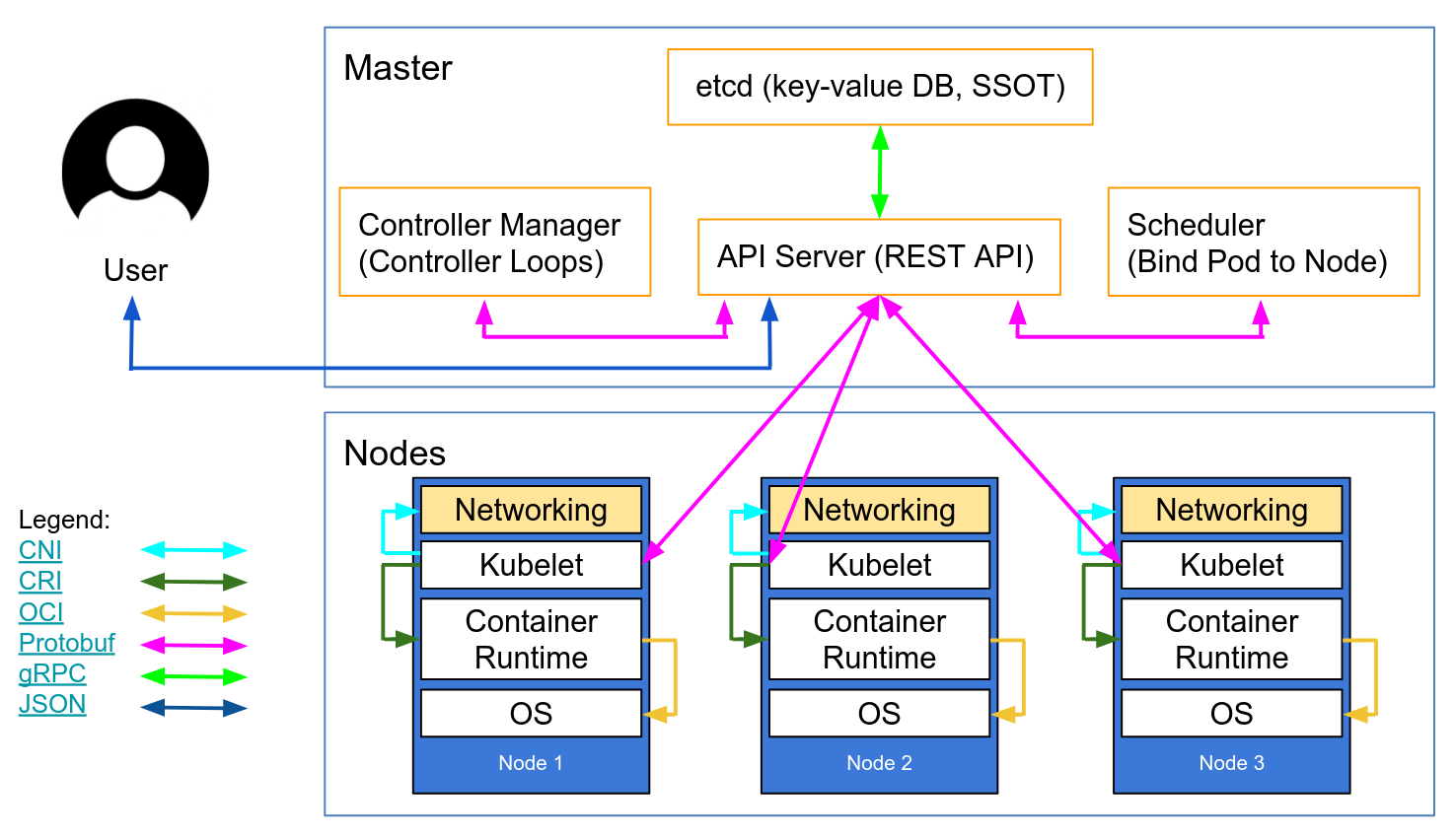
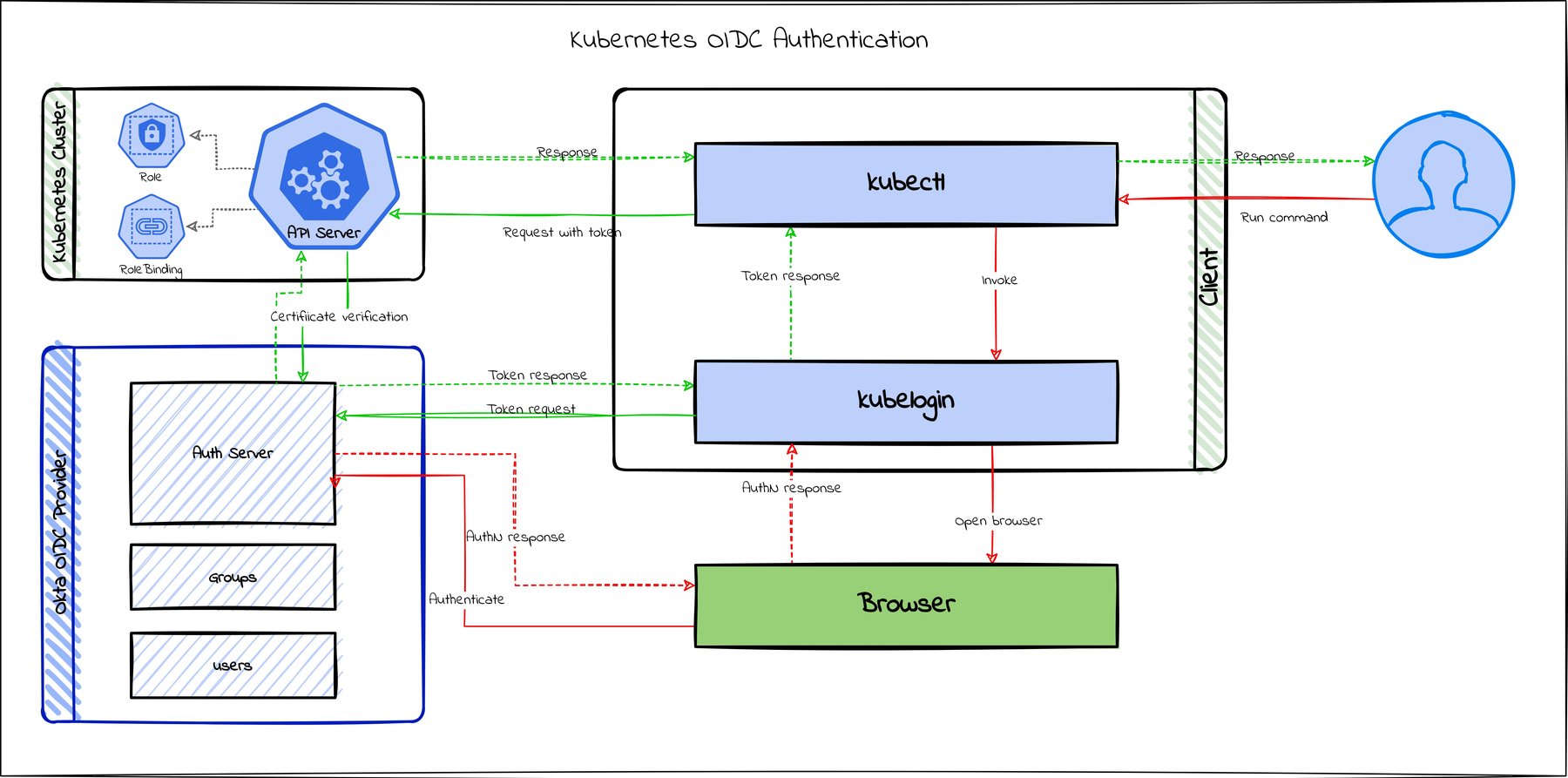
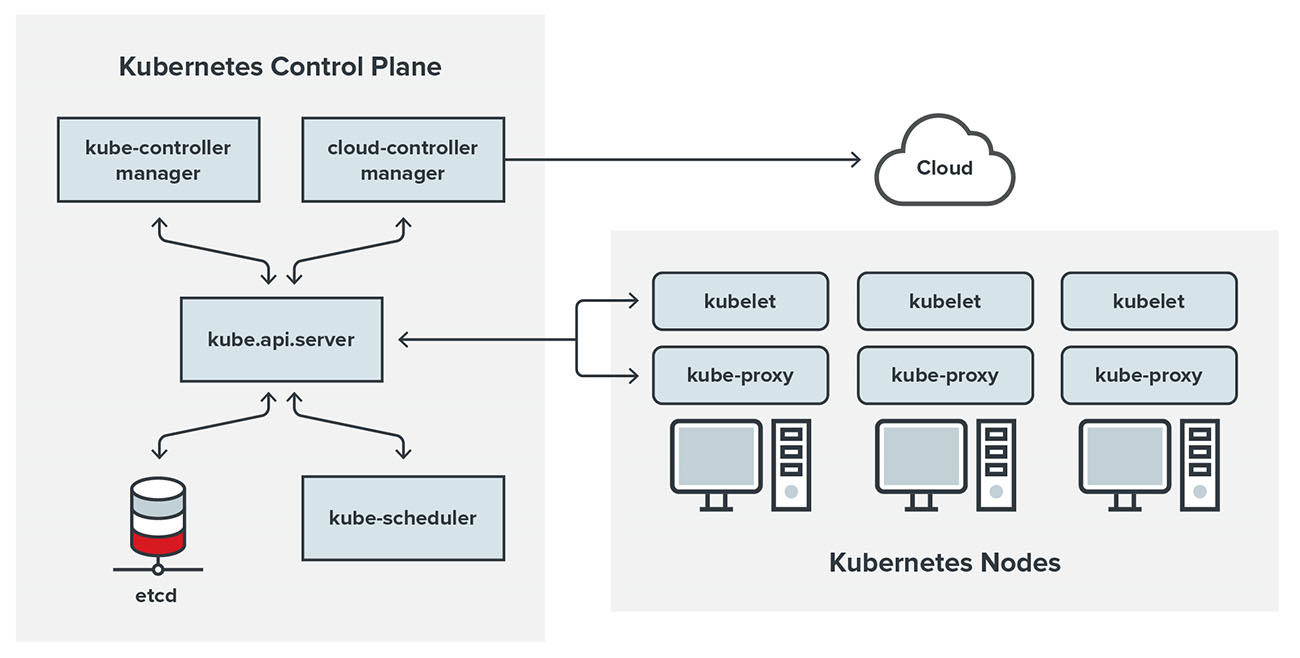
Future Internet | Free Full-Text | Vendor-Agnostic Reconfiguration of Kubernetes Clusters in Cloud Federations
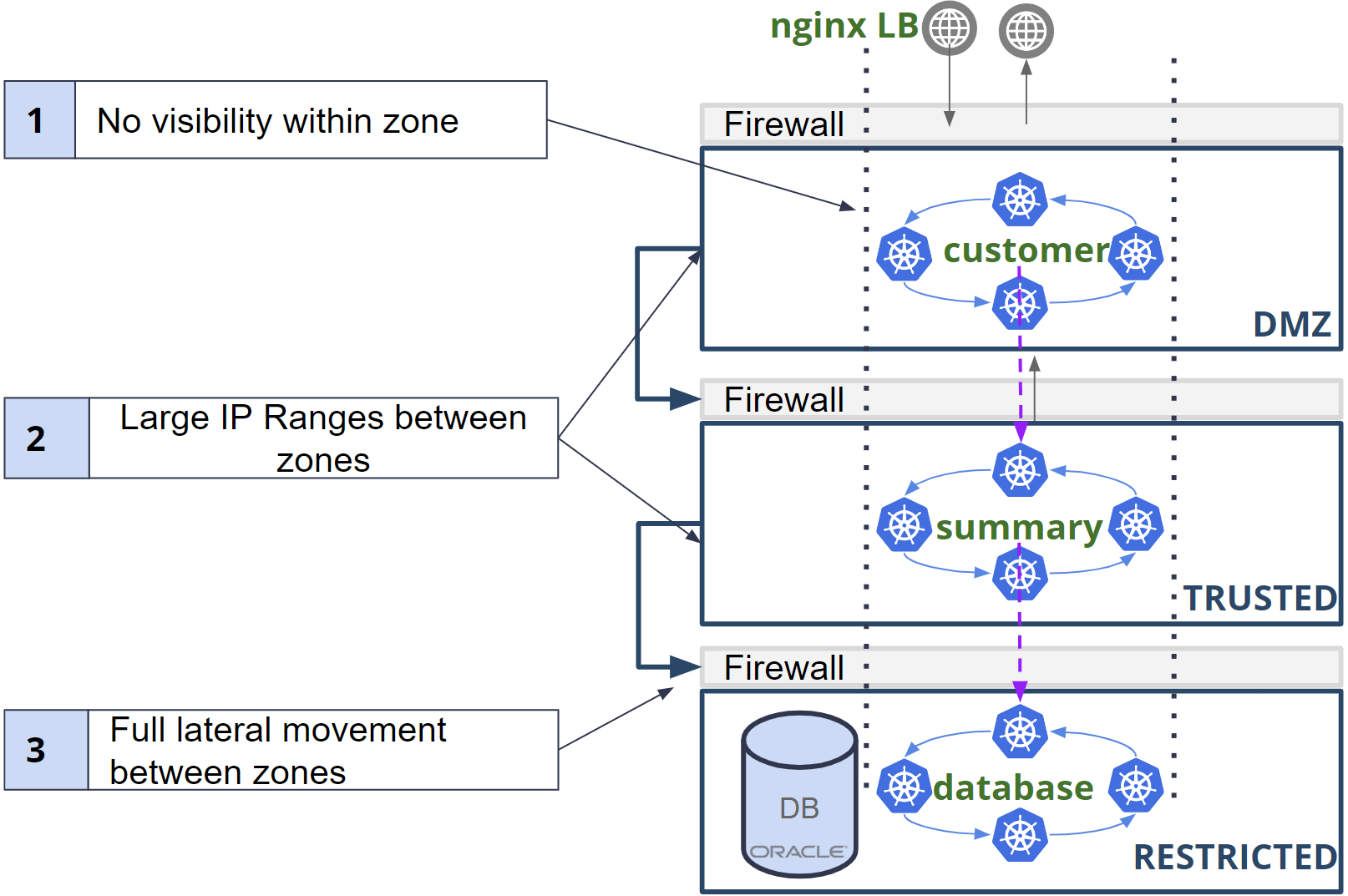
Kubernetes network security foundations: Get started on building your Kubernetes network security policies with Calico!
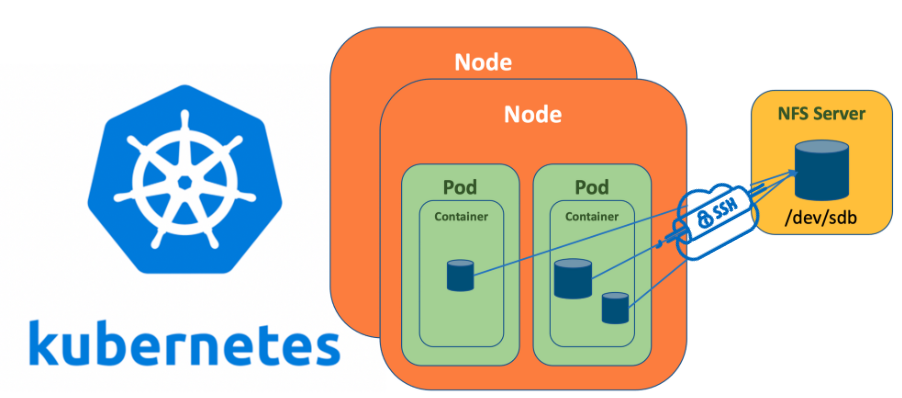
Ramkumar Krishnan: Kubernetes NFS encrypted communication: Kubernetes pod applications (as NFS client) and Linux based machine (as NFS server) – secure traffic using Tunnel Over SSH