5 steps to Risk Assessment: Step 5 - Review - System Concepts Ltd. Making places, products and services more usable, accessible and safe.

Security Risk assessment Template Lovely Security Risk assessment Template Excel Euthanasiapaper | Mission statement template, Assessment, Risk matrix

5 steps to Risk Assessment: Step 4 - Record your findings - System Concepts Ltd. Making places, products and services more usable, accessible and safe.

Accounting Information System Risk Assessment Algorithm Based on Analytic Hierarchy Process | Semantic Scholar


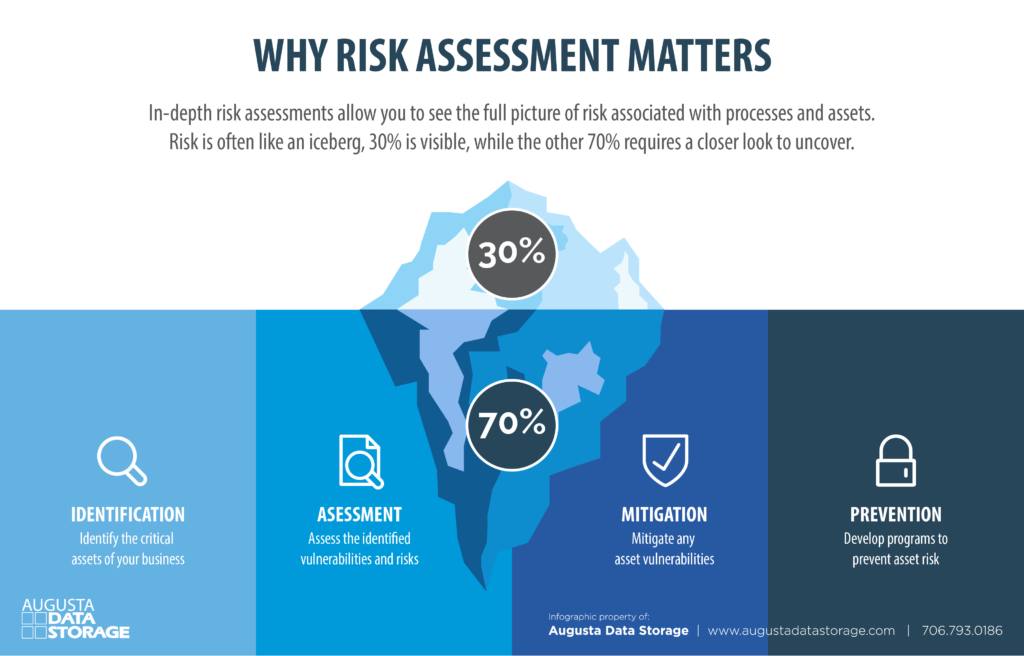
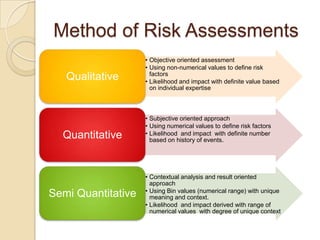
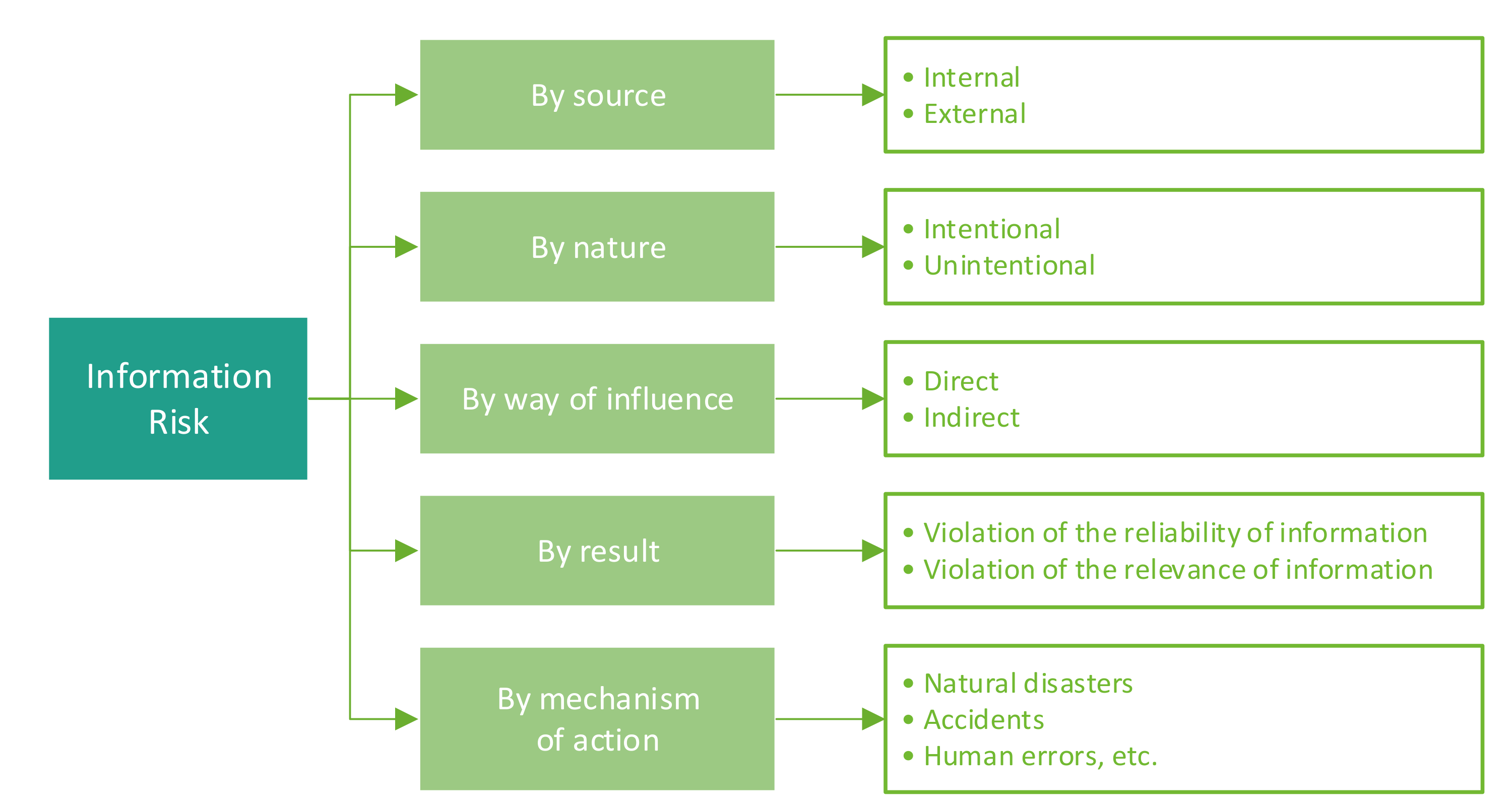

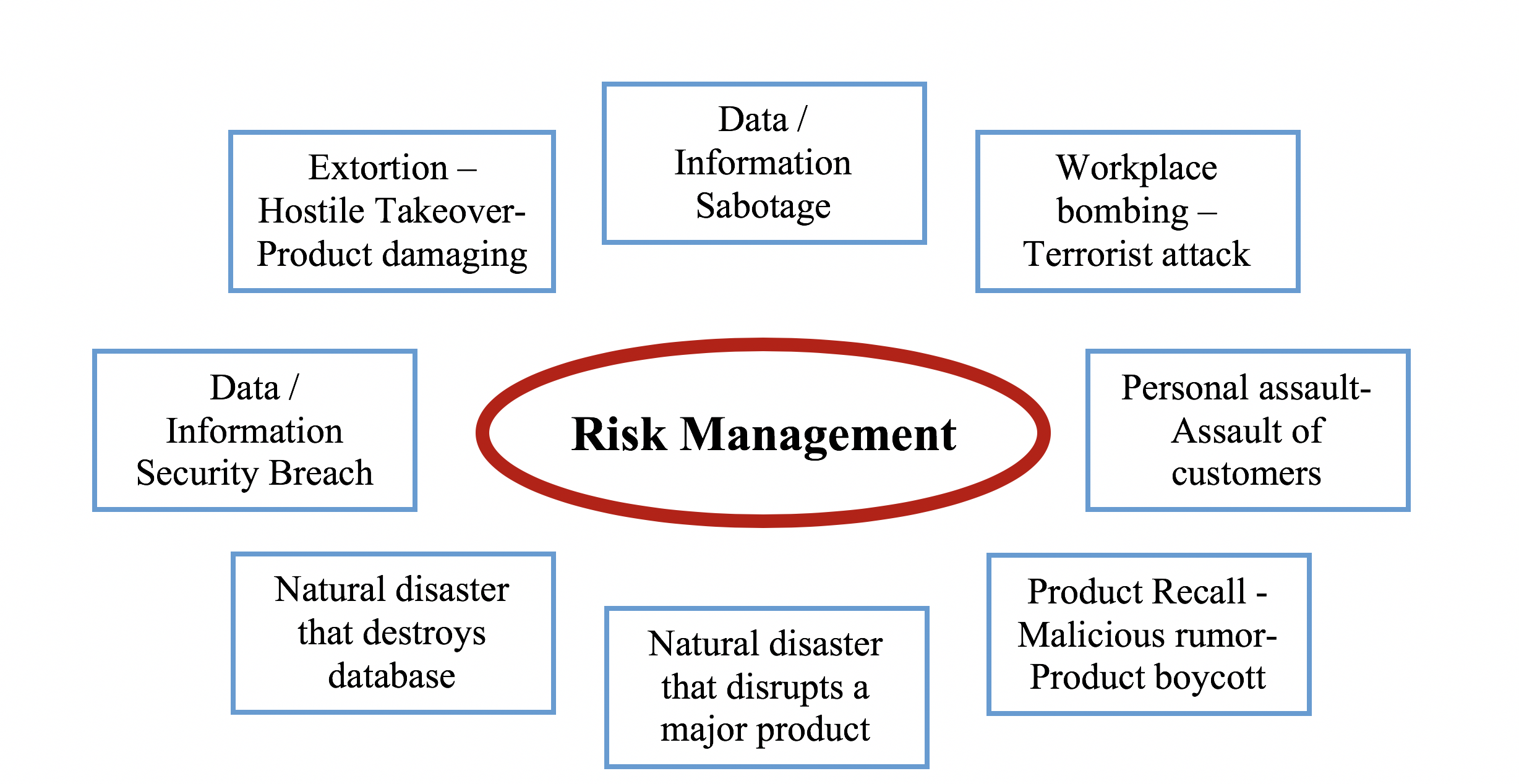

![PDF] Information Security Risks Assessment: A Case Study | Semantic Scholar PDF] Information Security Risks Assessment: A Case Study | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2c0857b159ab5488b90c1f112205f23e71b2b644/5-Figure2-1.png)