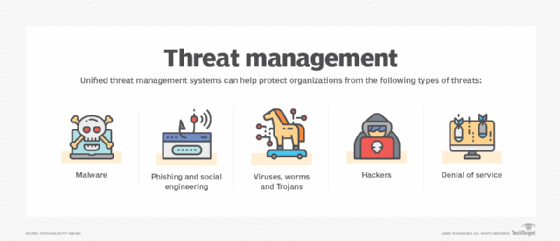
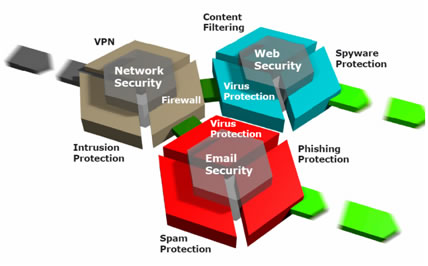
What Is Unified Threat Management (UTM)? Definition, Best Practices and Top UTM Tools for 2021 - Spiceworks

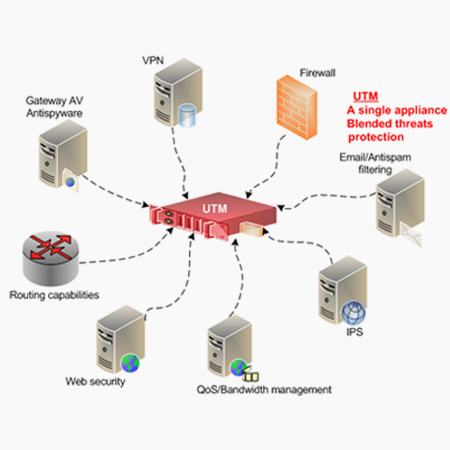
Yukta Agarwal on LinkedIn: #unifiedthreatmanagement #security #cybersecurity #integratedthreatdefense…

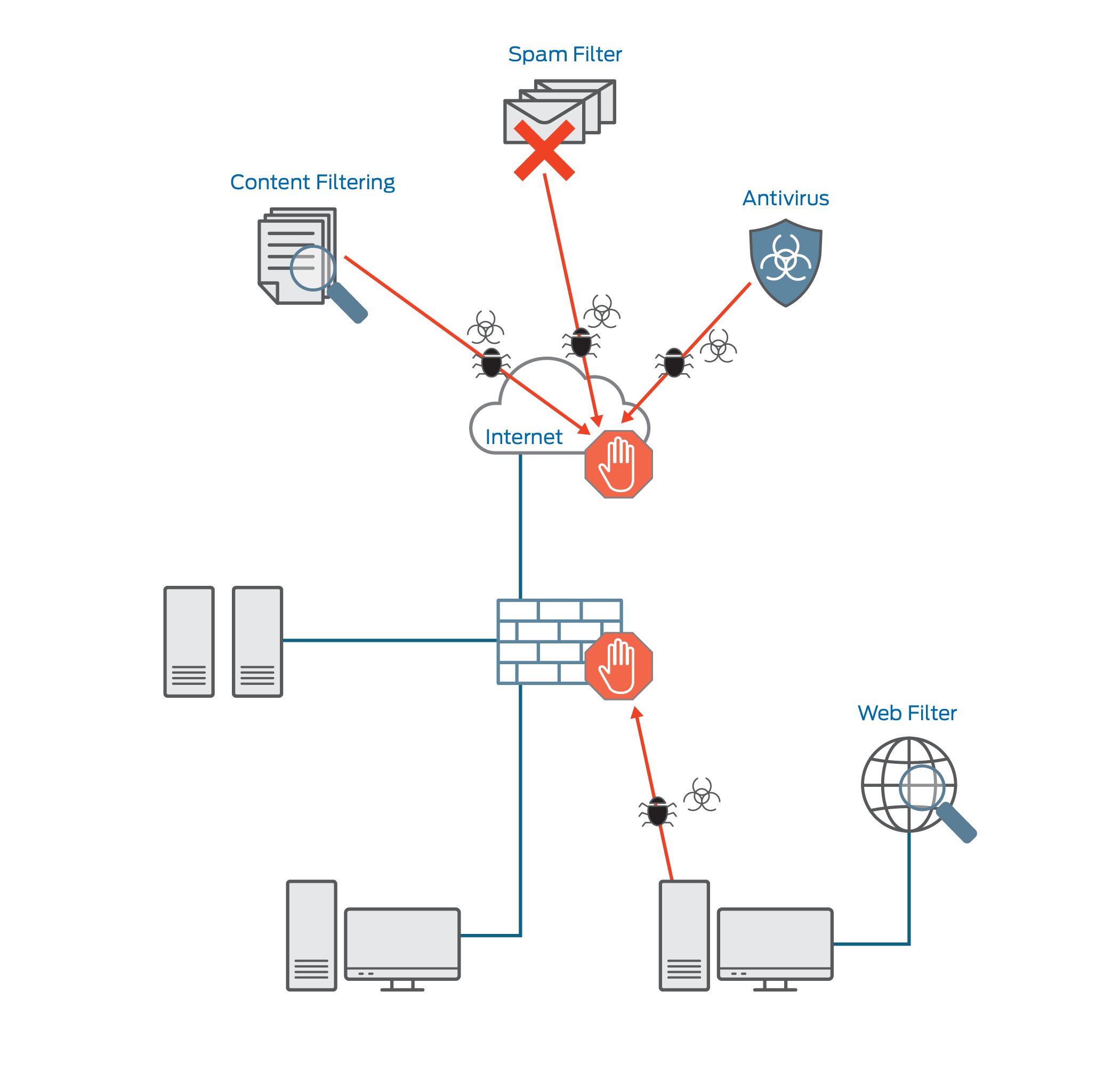
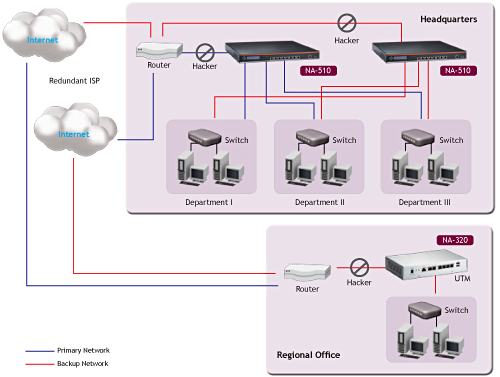
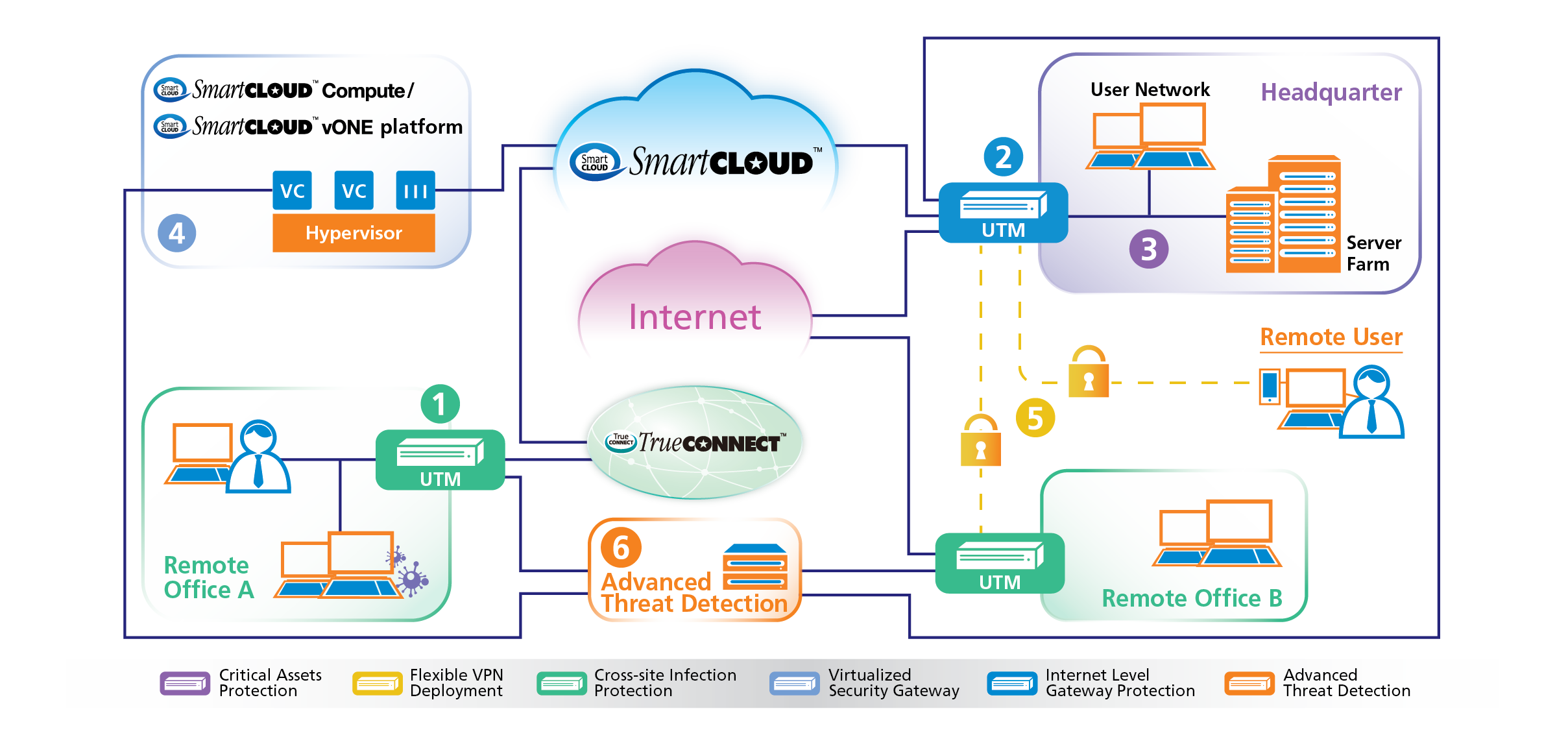
Figure 3 from Unified Threat Management System Approach for Securing SME's Network Infrastructure | Semantic Scholar

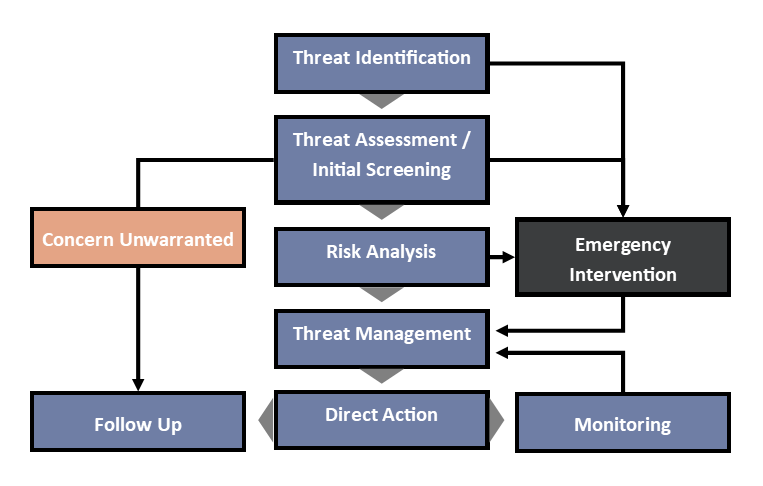
Cyber Threat Monitoring Systems - Comparing Attack Detection Performance of Ensemble Algorithms | SpringerLink